

October 31, 2023

Vinugayathri Chinnasamy

7 min Read
Over 75% of all cybercrimes primarily target web applications and their vulnerabilities. Attackers focus on exploiting weaknesses such as design flaws, vulnerabilities in APIs, open-source code, third-party widget issues, and access control problems. A recent study predicts that all this cybercrime will cost a massive $5.2 trillion by 2024 across all industries. How do you protect your web application from all the risks out there? Here is a go-to web app security checklist to get started.
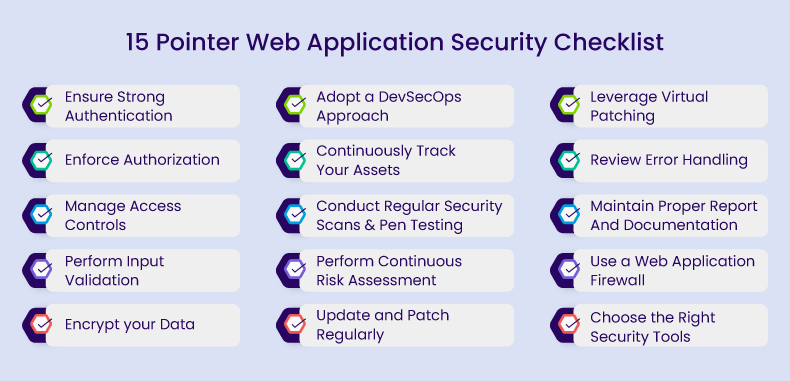
Without proper authorization controls, unauthorized access, data breaches, and potentially malicious activities are risky. By implementing robust authorization, you can ensure that sensitive data and functionalities are only accessible to authorized users, reducing the attack surface and enhancing overall security.
To ensure proper authorization, consider the following:
Proper access controls are important for various reasons:
Even a simple name or a photo uploaded can become trouble if not checked properly. It’s like letting a stranger in without asking who they are. This could lead to your website crashing or sensitive data being exposed.
To ensure your web app runs smoothly and stays safe, validating and verifying everything in users’ input is crucial. This way, you create a secure online environment while providing a positive experience for your users.
Here’s how to ensure proper input validation:
The next vital component of your web application security checklist is data encryption. It involves encoding sensitive information to protect it from unauthorized access and maintaining data confidentiality. Here’s what to consider for data encryption in your web application:
A DevSecOps approach incorporates security experts into the development process, seamlessly integrating security testing at every phase of the software development lifecycle. This includes automating security controls, particularly within the CI/CD pipeline, which is crucial for constructing a secure web application from its inception rather than treating security as an add-on.
A wide range of security tools are used in DevSecOps to achieve high automation levels and enhance the security of web applications during their development. Check out our detailed blog on the vital role of WAAP platforms in the CI/CD Pipeline.
Attackers like to target forgotten or shadow assets because they are easier to test without causing damage to active sites.
Visibility is the initial step to gain insight into your organization’s security posture. After all, you can’t protect what you can’t identify. It’s crucial to precisely understand the assets that compose your applications and software production infrastructure. This knowledge forms a cornerstone of your web application security checklist.
Follow these best practices to ensure an efficient asset discovery process:
Two crucial elements your web application security checklist cannot be complete without are:
Intelligent scanners run automatically on a daily and on-demand basis to keep identifying all known vulnerabilities in the application. The scanners systematically analyze various application components, including input fields, APIs, and databases, to identify potential security flaws such as SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF).
Conducting penetration testing is essential for uncovering security vulnerabilities throughout your web application, incorporating its backend and databases. Unlike automated tools, manual testing by certified experts can reveal unknown vulnerabilities and business logic flaws.
Incorporate the best practices outlined in our web application penetration testing checklist blog to assess your security posture.
The embedded DAST scanner within AppTrana can be tailored to perform daily scans on web and API applications or at a frequency of your choice. It augments automated assessments with manual penetration testing conducted by security experts who identify business logic vulnerabilities.
In 2021, organizations lacking a zero-trust approach incurred an average breach cost of $1.76 million higher than organizations that embraced zero trust as a security strategy.
While apps are not entirely un-hackable, risk assessment and prioritization help you set realistic goals, policies, and security standards. You need to keep assessing your organization’s risks and keep them within your tolerance levels.
Your assessments should address the following queries:
It is not enough for you to identify vulnerabilities; they must be immediately remediated. Security patches are updates aimed at fixing identified security vulnerabilities. These should be applied as soon as they become available.
This practice ensures that your web application remains resilient against emerging threats, minimizes the risk of security breaches, and upholds data integrity, user trust, and compliance with regulatory requirements, making it a critical and ongoing element of your security strategy.
There are scenarios where software vendors may not have released patches for known vulnerabilities, or applying patches may disrupt critical operations. Virtual patching provides an effective alternative.
Virtual patching is a rule set or configuration that blocks exploitation attempts and mitigates risks until a permanent fix is available. By doing so, virtual patching minimizes the window of opportunity for attackers, reducing the likelihood of successful exploits. This dynamic approach is particularly valuable in protecting applications from zero-day vulnerabilities or where patch deployment could lead to operational disruptions.
AppTrana can virtually patch high-risk vulnerabilities and stop attacks directly at the WAAP without requiring code modifications. This presents an excellent opportunity to decrease the vulnerability exposure period, allowing development and quality assurance (dev/QA) processes to catch up and apply patches to the code later.
This is another indispensable element of the web application security checklist. When logging into a web app, if the user encounters a detailed error message stating, “The password you entered is incorrect; please try again.” While this seems helpful for him, it could be a gift to a cybercriminal.
To prevent this, use concise error messages like “Invalid username or password.” Avoid giving clues or sensitive information and ensure consistency in error messages. Inconsistencies may inadvertently reveal information to malicious actors, so it’s important to maintain a uniform approach.
Imagine a security breach occurs, and your organization needs to respond quickly and effectively. Proper documentation in this context would involve having an incident response plan, clear records of what security measures were in effect, and detailed logs of the breach, including its timeline, affected systems, and the actions taken to contain and mitigate the incident.
Thanks to thorough documentation, the security team can promptly identify the breach source of the compromised data and implement countermeasures to mitigate further damage.
This expedites recovery, helps assess the incident’s impact, and provides vital compliance and risk assessment information. Furthermore, consistent documentation helps track security improvements, strengthening the web application’s security posture.
WAF plays a vital role in protecting web applications against dangers from compromised or malicious endpoints, functioning as reverse proxies rather than traditional user-focused proxy servers.
One of the key advantages of WAF lies in its agility, allowing for the quick adaptation of security policies to combat ever-changing attack vectors. For instance, during a DDoS attack, the WAF can promptly apply rate-limiting measures through policy modifications. Check out the six key considerations in deploying a WAF, here.
Your web application security tools should not merely function as repair agents like traditional antivirus software. Instead, they should act as collaborative allies, providing invaluable support to your security team and web application developers in various capacities, including offering proof, expertise, monitoring, and management.
A critical decision-making factor is the issue of false positives. When security engineers or developers cannot trust the accuracy of a tool’s alerts, they are compelled to validate every piece of information it provides. It is recommended to choose the vendor who are bundled with managed service to handle the false positives.
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn.
Vinugayathri is a dynamic marketing professional specializing in tech content creation and strategy. Her expertise spans cybersecurity, IoT, and AI, where she simplifies complex technical concepts for diverse audiences. At Indusface, she collaborates with cross-functional teams to produce high-quality marketing materials, ensuring clarity and consistency in every piece.